Empowering Developer Productivity through Platform Engineering on AWS
At copebit, enabling developers to rapidly innovate without infrastructure constraints is crucial. Over the past decade, as organizations faced increasing complexity in managing their technical infrastructure, many turned to DevOps practices to accelerate software delivery and improve collaboration. While DevOps brought important cultural and technical improvements, it also revealed new challenges—such as fragmented tooling, inconsistent environments, and duplicated efforts across teams.
As a response, platform engineering emerged not as a replacement for DevOps, but as a complementary discipline. It introduces dedicated teams focused on designing and maintaining internal developer platforms that abstract away infrastructure complexity through automation, standardization, and self-service capabilities.
Today, copebit’s advanced platform engineering strategy builds on core DevOps principles and extends them using elastic infrastructure concepts, deep integration with cloud-native technologies, and a strong focus on developer experience. This creates a robust and scalable self-service environment, empowering developers to focus fully on innovation and software development.
Deep Dive into Platform Engineering
Platform engineering at copebit involves creating internal, self-service platforms designed to simplify application deployment, resource provisioning, and service management. The complexity of modern cloud-native environments introduces challenges such as managing infrastructure at scale, ensuring security, maintaining consistency across multiple environments, and avoiding configuration drift. Developers often face long wait times for infrastructure provisioning, inconsistent development environments, and operational overhead when managing their own deployments.
To address these challenges, copebit’s platform engineering approach centralizes infrastructure management, offering standardized environments, automated workflows, and self-service capabilities. By leveraging Infrastructure-as-Code (IaC) tools such as OpenTofu, the platform team ensures that every resource is provisioned predictably, is version-controlled, and follows strict governance policies. Automated CI/CD pipelines further enhance this process by enforcing security and compliance at every stage.
The foundation of copebit’s platform engineering strategy lies in elasticity, automation, and declarative configuration. Kubernetes-based workloads, GitOps practices, and service orchestration ensure that infrastructure is dynamically adjusted based on demand, minimizing operational overhead while maximizing efficiency. Observability tools provide real-time insights into system health, while secure, immutable deployments guarantee consistency across environments.
Ultimately, copebit’s platform engineering model transforms infrastructure from a bottleneck into an enabler. Developers no longer need to worry about resource provisioning, security enforcement, or deployment inconsistencies. Instead, they gain access to an optimized, scalable, and self-service development environment, allowing them to focus on delivering high-quality applications without infrastructure concerns.
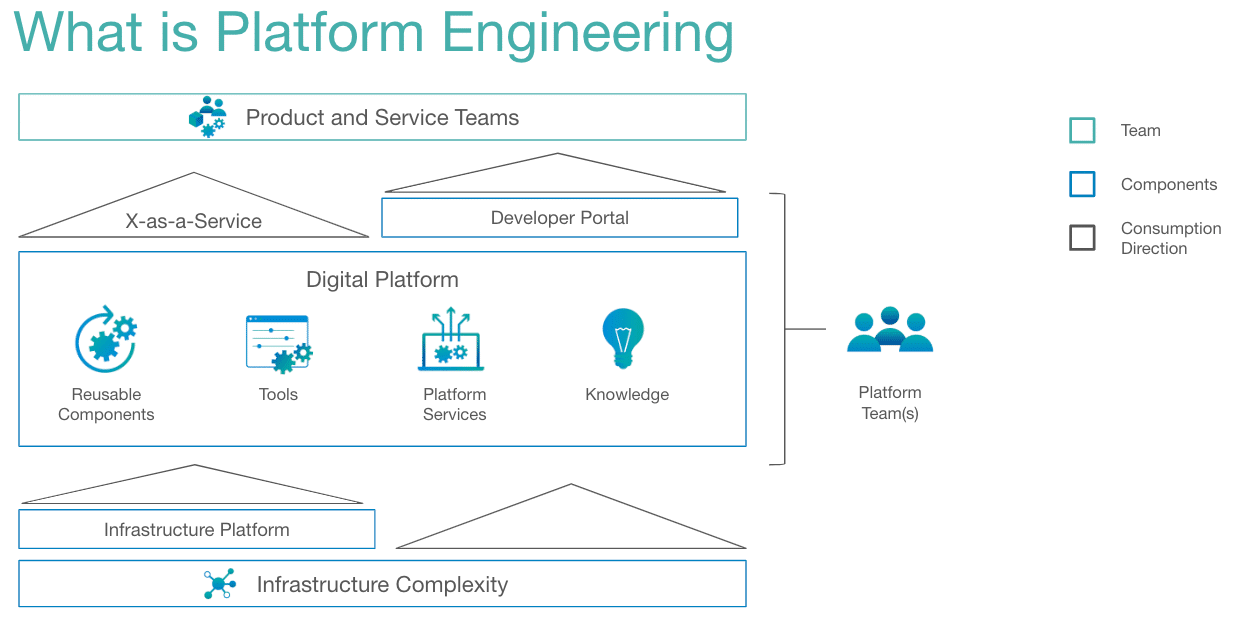
What Platform Engineering Really Means
Platform engineering is not a replacement for DevOps, but rather a natural evolution and specialization within the DevOps ecosystem. While DevOps emphasizes cultural change, automation, and team collaboration, platform engineering focuses on building internal developer platforms (IDPs) that enable DevOps at scale — especially in complex, multi-team cloud environments.
These platforms provide standardized, reusable tools and services that abstract away the complexities of cloud infrastructure. At copebit, platform engineering supports — but does not replace — DevOps practices. It empowers development teams by giving them a consistent, self-service interface for deploying services, managing infrastructure, and maintaining secure, observable environments.
Key Components of Platform Engineering at copebit
- Internal Developer Platform (IDP):
A curated set of tools, services, and workflows provided as a self-service interface to development teams. This includes:
– CI/CD pipelines
– Kubernetes orchestration
– Infrastructure-as-Code with OpenTofu
– Logging, monitoring, and tracing (e.g., Prometheus, Grafana)
– Secrets management and automated policy enforcement - Self-Service Capabilities:
Developers can launch services, provision infrastructure, or configure environments independently, without needing deep cloud or Kubernetes expertise — significantly reducing time-to-value. - Standardization and Governance:
Reusable modules (e.g., Terraform templates, Helm charts), centralized access controls, and pre-approved configurations ensure consistency, compliance, and security across teams and environments. - Elastic and Declarative Infrastructure:
Platform behavior is defined declaratively and adjusts automatically to load and resource demands, thanks to GitOps workflows and container orchestration via Kubernetes. - DevOps Enablement, not DevOps Doing:
The platform team builds and maintains the infrastructure and automation that development teams use — allowing them to practice DevOps effectively without managing its complexity themselves.
Platform Engineering contrasted to Traditional DevOps
The AWS Context
In AWS environments, a typical internal developer platform might include:
- VPCs, EKS clusters, and databases provisioned via IaC (e.g., OpenTofu, CloudFormation)
- CI/CD via AWS CodePipeline or GitHub Actions
- Pre-approved service blueprints and IAM policies
- Observability tools like CloudWatch, X-Ray, Prometheus
- Developer portals powered by tools like Backstage
This structured approach ensures security, reliability, and scalability — even in large, distributed teams.
The Strategic Value
copebit’s platform engineering initiative accelerates software delivery while improving security, consistency, and operational efficiency. It scales DevOps beyond isolated teams and empowers organizations to innovate faster — without sacrificing control or compliance.
Platform engineering turns infrastructure from a reactive, manual effort into a strategic asset: reliable, scalable, and built for developer productivity.
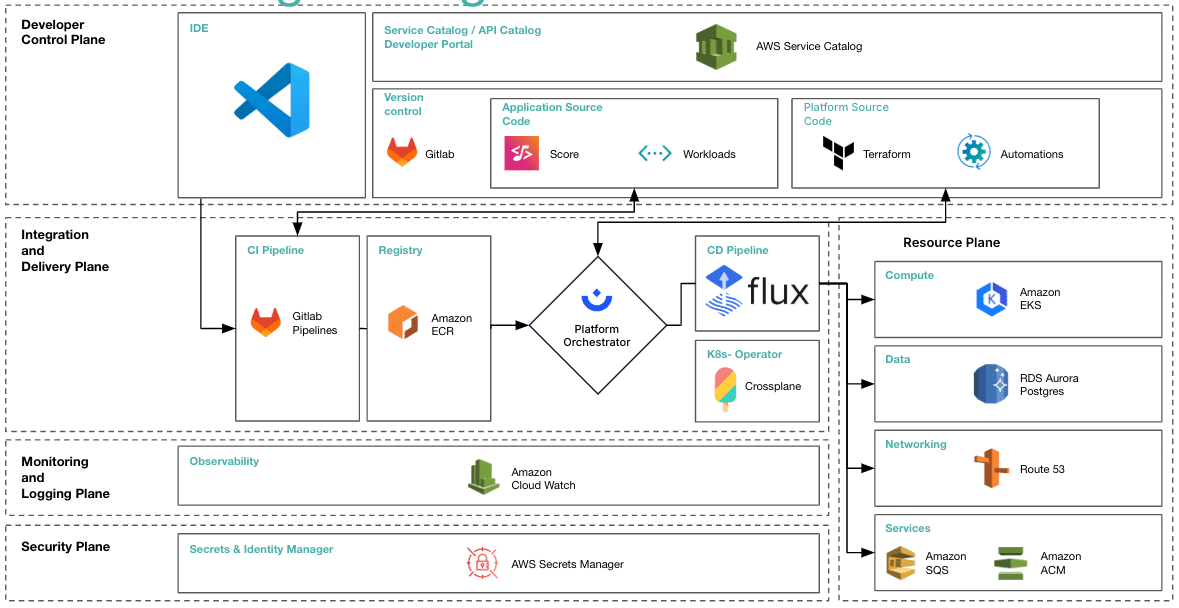
Technical Pillars of copebit’s Platform Engineering
We use Infrastructure-as-Code (IaC) with OpenTofu to manage AWS infrastructure, ensuring consistency and transparency. copebit also uses GitLab CI/CD and GitHub Actions for Continuous Integration and Continuous Delivery (CI/CD) to automate and speed up software delivery. To ensure security, copebit integrates security measures into CI/CD workflows, including automated security scans, vulnerability assessments, and secure secrets management with AWS Secrets Manager. Container scanning is done through AWS ECR, and GitLab pipelines are used for automated code scanning.
Technical Elements of Platform Engineering
copebit’s Elastic Infrastructure: Technical Foundations
Elastic infrastructure dynamically allocates resources in real-time. copebit specifically leverages AWS Elastic Kubernetes Service (EKS), auto-scaling techniques, and GitOps practices. Read more on an Elastic Infrastructure here
AWS Elastic Kubernetes Service (EKS) with EKS Auto-mode
copebit’s EKS implementation leverages AWS’s innovative capabilities to substantially reduce operational complexity. EKS Auto-mode simplifies operations by automatically managing essential infrastructure components, including load balancing, storage provisioning, and observability configurations. For instance, it automatically provisions load balancers, dynamically attaches persistent storage, and sets default CloudWatch metrics and alarms during new application deployments. Additionally, EKS Auto-mode seamlessly integrates Karpenter’s nodepool functionality, eliminating the need for separate installations. Karpenter automatically provisions and manages nodes based on real-time pod requirements, optimizing infrastructure scaling.
Read more on EKS Karpenter here
Elastic Databases and Messaging
We employ advanced AWS serverless database and messaging technologies:
- Amazon Aurora Serverless v2: Dynamically scales database capacity, enabling seamless scalability without manual intervention.
- ElastiCache Serverless: Provides managed caching services that dynamically scale, enhancing application performance and reducing latency.
- Elastic Kafka with MSK Serverless: Offers fully managed Kafka clusters that automatically scale based on demand, simplifying administration and reducing infrastructure overhead.
GitOps with FluxCD
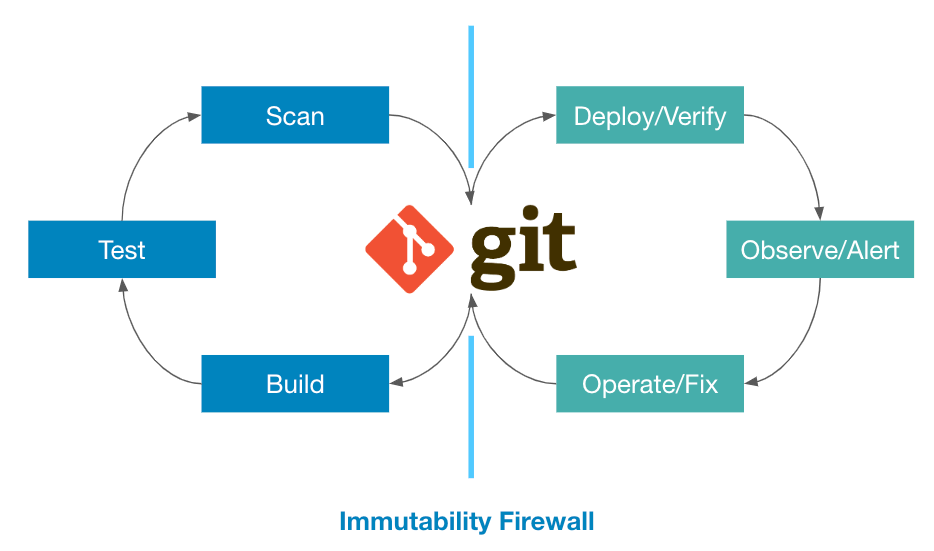
copebit extensively employs FluxCD for automating infrastructure and application lifecycle management via GitOps. GitOps as a concept emerged to bring infrastructure management closer to software development best practices, ensuring version-controlled, auditable, and automated deployments. Historically, infrastructure provisioning was a manual and error-prone process, often leading to inconsistencies across environments. Flux was developed to solve these challenges by enforcing declarative infrastructure through a Git-based workflow. It ensures that what is stored in the repository is what gets deployed, eliminating configuration drift and providing an immutable source of truth:
- Automated Reconciliation: Flux continuously ensures Kubernetes clusters match definitions stored in Git.
- Real-time Drift Detection and Correction: Automatically detects and corrects configuration drift, maintaining system integrity.
- Multi-Cluster and Multi-Environment Management: Simplifies Kubernetes management across multiple clusters and environments using a centralized Git repository.
- Immutability Firewall: Ensures only configurations explicitly defined in Git are deployed, minimizing risks associated with manual changes. For example, when developers commit Kubernetes manifests, Flux automatically enforces these exact configurations across environments.
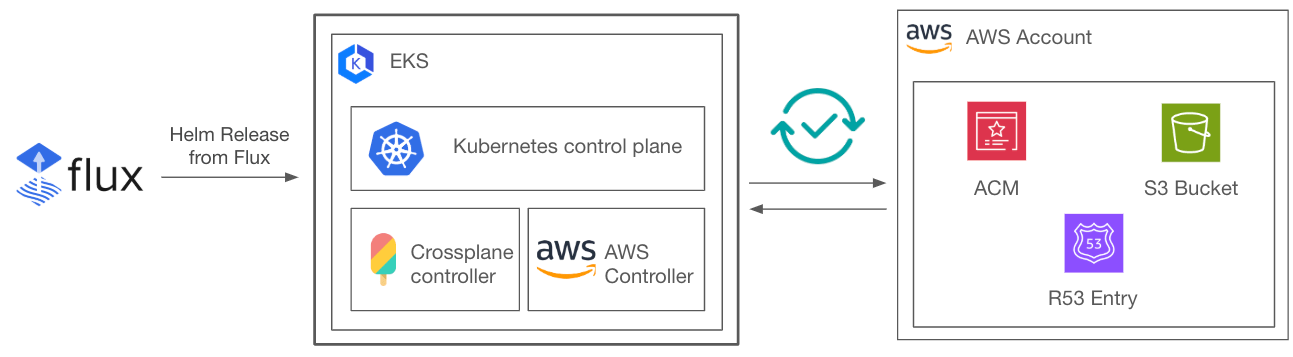
Advanced Infrastructure Provisioning with Crossplane
Crossplane streamlines cloud resource provisioning directly through Kubernetes. It was developed to address the growing complexity of managing cloud infrastructure across multiple providers, where traditional IaC tools often fell short in providing a unified, Kubernetes-native approach. By extending the Kubernetes API, Crossplane allows platform teams to define and manage cloud resources using Custom Resource Definitions (CRDs), eliminating the need for external provisioning tools.
Crossplane helps organizations standardize cloud resource provisioning by leveraging Kubernetes’ declarative model. This ensures that infrastructure resources such as databases, storage, and networking are defined as code and automatically reconciled to match their desired state. Unlike traditional IaC tools that require periodic execution, Crossplane continuously ensures infrastructure consistency in real-time.
For copebit, Crossplane plays a crucial role in enabling developers to request and manage infrastructure resources seamlessly. Instead of submitting manual infrastructure tickets, developers define their resource needs in Kubernetes manifests, and Crossplane provisions and maintains them autonomously. This self-service model drastically improves development velocity while maintaining governance and security standards.
Crossplane integrates with GitOps workflows to provide version-controlled, auditable, and repeatable infrastructure, aligning with copebit’s vision for an elastic, fully automated platform that empowers developers and reduces operational overhead.
As a universal control plane for AWS resources, Crossplane allows for centralized management of AWS resources across regions and accounts via Kubernetes. Additionally, it enables declarative provisioning of resources (e.g. S3 buckets, DynamoDB tables, and IAM roles) via Kubernetes manifests using Kubernetes CRDs. By using CRDs to define resources declaratively, developers can dynamically provision AWS infrastructure.
Comprehensive Security Practices
We enforce stringent security measures throughout infrastructure and application lifecycles:
- Automated Code Scanning: GitLab CI/CD pipelines continuously scan for vulnerabilities, ensuring secure deployments.
- Container Security: AWS ECR scans container images to proactively identify and resolve vulnerabilities.
- Secrets Management: AWS Secrets Manager securely stores and rotates sensitive credentials.
- Continuous Compliance and Auditing: AWS Config and Security Hub provide real-time auditing, ensuring proactive management of compliance and security.
Developer Portal for Enhanced Self-Service
It provides a dedicated developer portal offering:
- Centralized Resource Management: Simple interface for developers to autonomously request and manage cloud resources.
- Comprehensive Documentation: Detailed tutorials, FAQs, and resources for quick onboarding.
- Collaboration Tools: Facilitates effective communication between development and platform engineering teams.
For instance, a copebit client significantly reduced application onboarding from weeks to hours using the portal, accelerating resource provisioning and enhancing team collaboration.
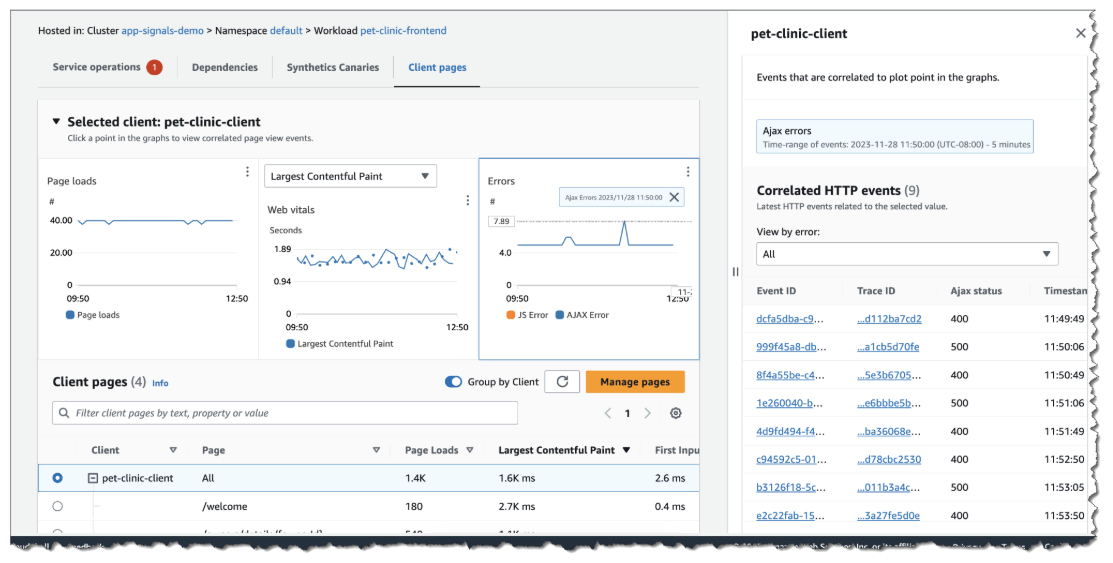
Observability and Monitoring
Deploys comprehensive observability solutions to improve visibility into system health and performance. In the context of platform engineering, observability is critical for maintaining system reliability, optimizing performance, and ensuring rapid issue resolution. Without proper monitoring, debugging distributed cloud-native architectures becomes complex, leading to increased downtime and reduced developer productivity.
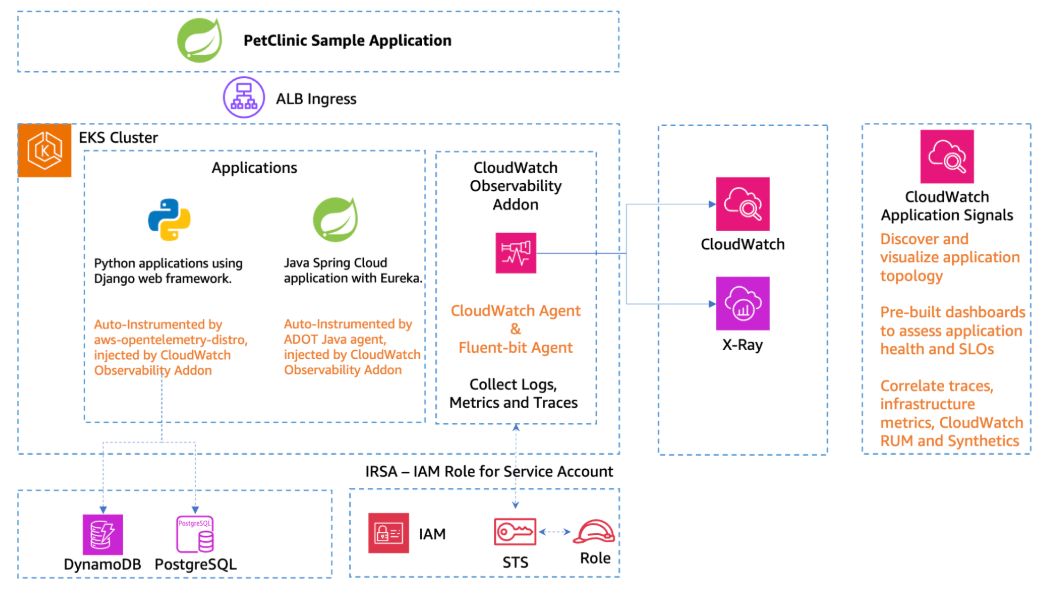
By integrating advanced monitoring tools, copebit provides proactive detection of infrastructure anomalies, allowing platform teams to address issues before they impact applications. AWS CloudWatch, introduced in 2009, revolutionized cloud monitoring in a cloud-native manner by offering detailed insights into infrastructure performance, setting the foundation for modern observability practices. Over time, the demand for more granular monitoring across distributed cloud-native architectures led to the evolution of advanced telemetry solutions.
AWS AppSignal, combined with AWS Distro for OpenTelemetry (ADOT), provides unified tracing, logging, and metrics collection, simplifying observability and reducing the reliance on expensive application performance monitoring (APM) solutions. Many organizations find that AppSignal, with its native AWS integration, is a cost-effective alternative to high-cost APM platforms while still offering deep insights into application health and performance.
Metrics, logs, and traces are continuously collected and analyzed, enabling full visibility into resource utilization, application health, and security posture. This data-driven approach supports auto-scaling decisions, improves incident response times, and enhances cost efficiency by optimizing resource allocation.
AWS Container Insights
Automatically provides detailed performance metrics and diagnostics for Kubernetes clusters.
AWS AppSignal with ADOT
Unified telemetry collection across traces, logs, and metrics, simplifying observability.
Prometheus and Grafana
Prometheus aggregates extensive metrics, while Grafana provides visual dashboards, facilitating quick issue resolution.
Managing Multiple Environments from a Single Codebase
Managing multiple environments presents challenges such as configuration drift and complex troubleshooting. copebit effectively addresses these challenges with a unified declarative approach:
- GitOps and Branching Strategies: Clear branching structures ensure consistent yet isolated environments.
- Declarative Configuration Management: Ensures repeatable, consistent deployments across various environments.
- Crossplane and FluxCD Integration: Automates seamless, declarative management of resources, significantly simplifying environment management from a single codebase.
Client Outcomes and Practical Benefits
Our clients realize significant advantages:
- Accelerated Development Cycles: Infrastructure automation accelerates deployments, enabling faster innovation cycles.
- Cost Optimization: Efficient resource scaling reduces infrastructure expenses.
- Operational Excellence: Automation shifts team focus from manual tasks to strategic innovation.
- Enhanced Security Posture: Integrated security automation maintains robust protection with minimal operational overhead.
Demonstration
Find a full Presentation here, including a demonstration:
Conclusion
The advanced platform engineering strategies on AWS, encompassing Kubernetes, EKS Auto-mode with integrated Karpenter nodepools, FluxCD, Crossplane, robust observability solutions, comprehensive security practices, and a dynamic developer portal, significantly boost developer productivity and operational agility. By automating complex infrastructure management, copebit enables developers to focus entirely on innovation, driving business growth, operational excellence, and sustained competitive advantage.