Enterprise-Grade Network and Container Security for Kubernetes
Over the past year, we at copebit have helped our clients to develop numerous container- and Kubernetes-based applications with our guidance. Throughout these projects, our expertise in crafting enterprise-standard container foundations has grown, emphasizing security, high automation, and optimal performance. In collaboration with our partner Isovalent, we’re advancing network and security solutions for containers to an advanced level level.
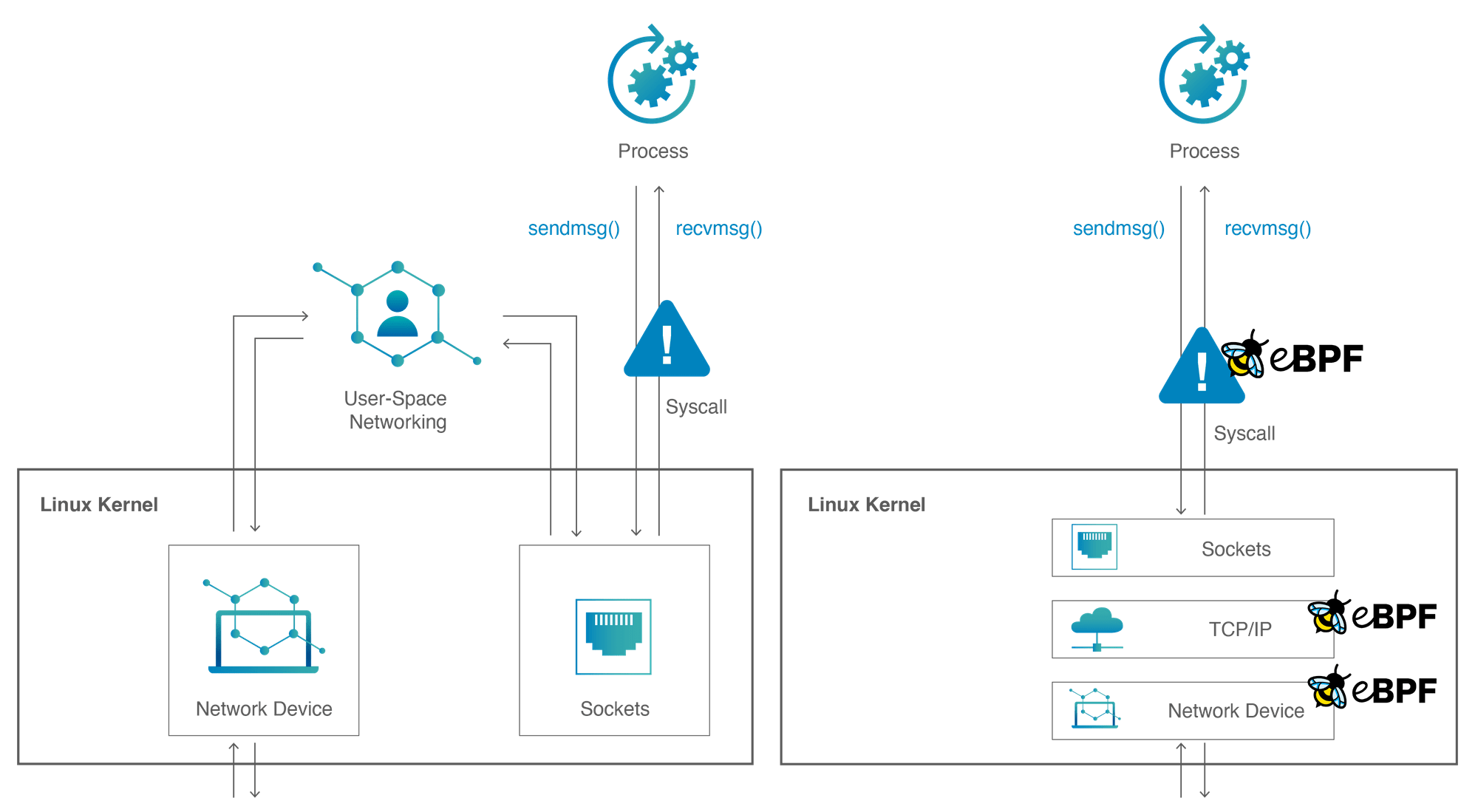
eBPF
The founders of Isovalent, who are among the inventors of eBPF, have deep roots in networking, security, and Linux kernel development. Their experience with large clients has shown that the traditional Container Network Interface (CNI) method, which oscillates between kernel and user space, hampers performance and provides limited functionality. Leveraging their expertise in eBPF, they engineered a groundbreaking solution that makes the Linux kernel programmable. This approach has not only led to the development of exceptional features but also forms the foundational element of Isovalent’s container-related solutions.
At copebit, there’s a focus on working with clients to adopt Cilium/Hubble as the primary CNI for enterprise Kubernetes environments. Additionally, copebit is exploring Tetragon, utilizing its robust security features
Cilium
Kubernetes, when implemented in a clustered environment, mandates a robust networking infrastructure. This includes essentials like forwarding, security, load balancing, and service discovery. copebit has traditionally utilized cloud-native CNI implementations, yet there’s a growing realization that these may not meet the high standards expected by enterprise clients. Many of these services are deeply connected with their respective cloud platforms. While often beneficial, this integration poses unique challenges within Kubernetes environments, such as IP address exhaustion and increased complexity in delineating platform and application responsibilities. This is especially visible in larger organizations where multiple teams manage container platforms at scale, necessitating a clear separation between platform and application teams. The adoption of Cilium as a CNI solution offers a highly efficient and reliable alternative, boasting adoption by large-scale enterprises and introducing innovative features not available in standard CNI offerings.
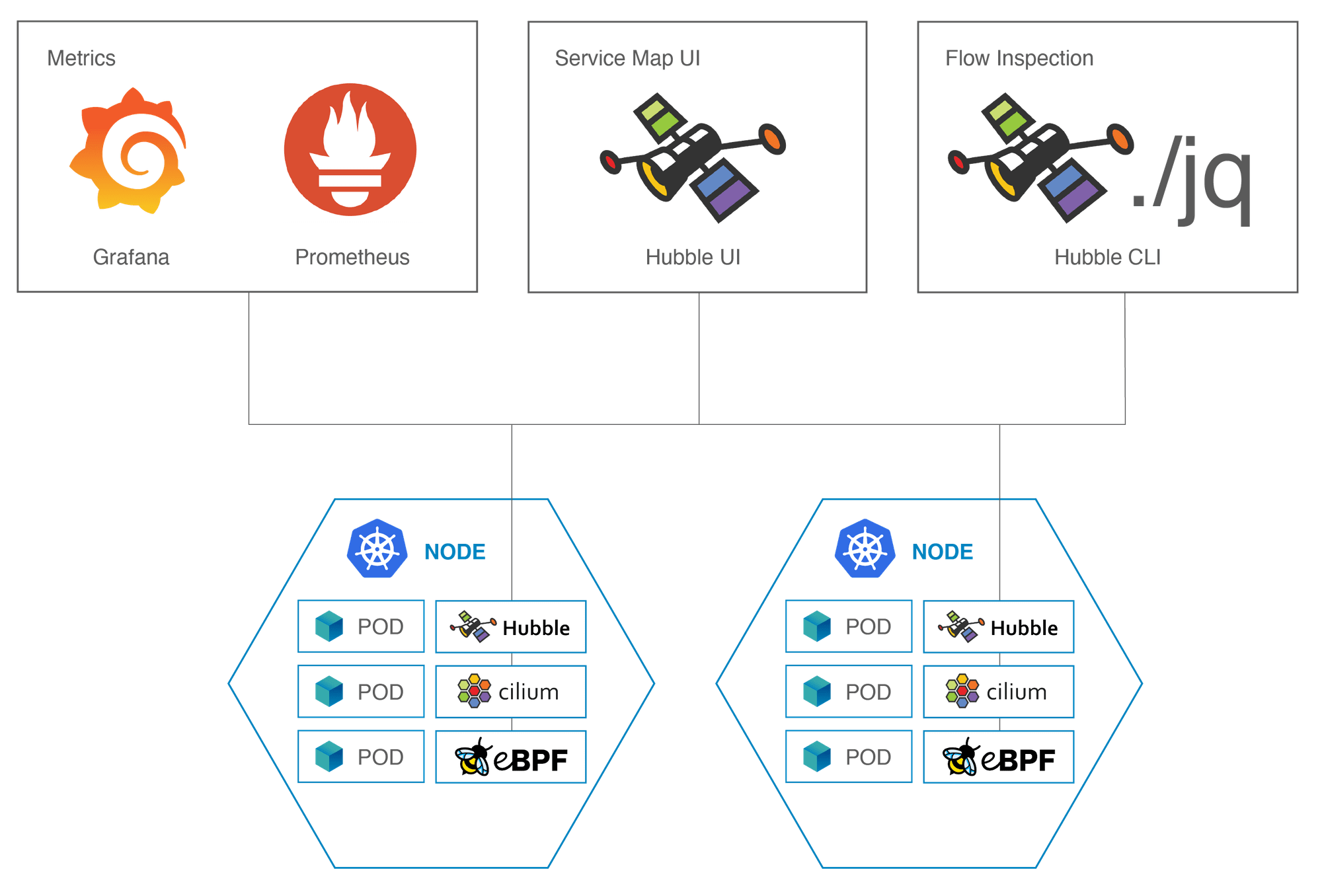
Hubble
Enterprises must adhere to industry-specific regulations for application security. This is especially crucial in sectors like finance and healthcare, which have very strict standards. A common practice among such firms involves implementing network policies in their Kubernetes clusters to manage traffic flow. However, this often creates challenges during solution development due to uncertainties about allowed protocols and necessary communication patterns, particularly when these policies are applied to long-running applications. Hubble emerges as an ideal tool for illuminating all network activity within a Kubernetes cluster. It logs and displays every transmitted byte in the Hubble console. Thus, Hubble not only reveals ongoing traffic but also identifies traffic blocked by network policies. copebit advises clients who employ network policies to integrate Hubble. This enhances visibility, facilitates network policy management, and provides comprehensive insights into cluster traffic patterns.
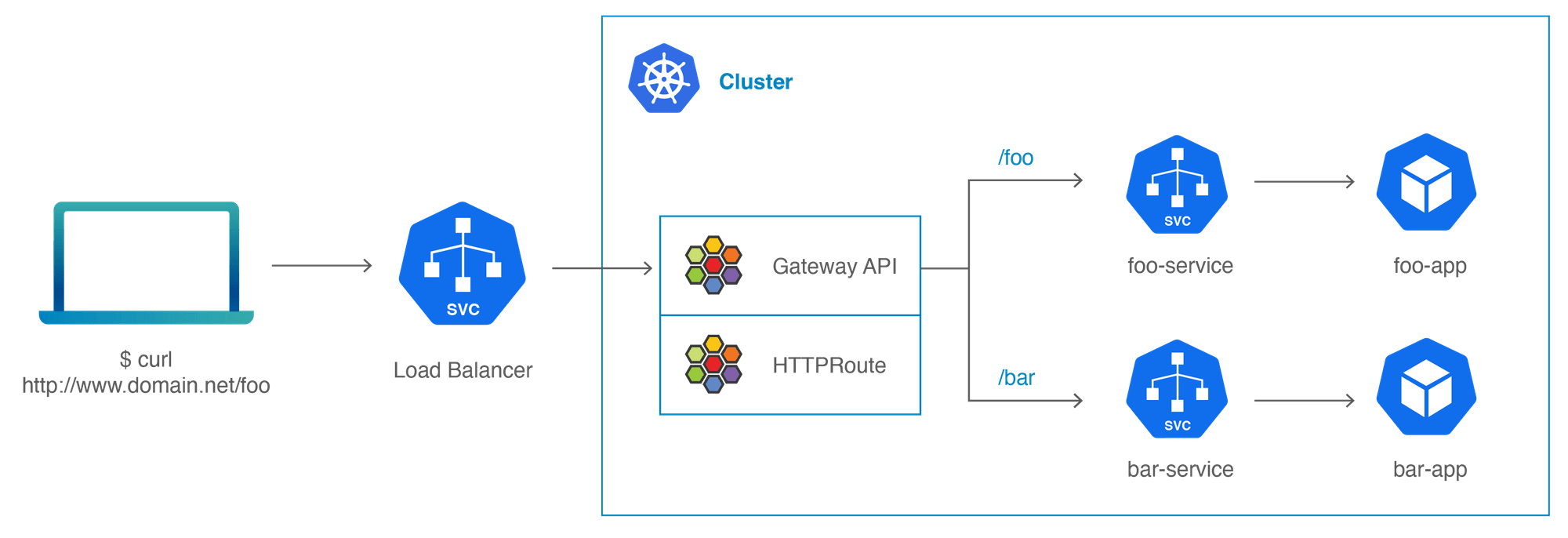
Ingress and Service Mesh with Cilium
Applications requiring external cluster access need specific ports or paths open. Historically, this was achieved using node ports, load balancers, and ingresses. Cilium enhances this process by offering superior performance and security.
Cilium’s advanced built-in ingress operates directly in kernel space using eBPF. This approach not only boosts performance but also removes the need for an additional third-party ingress controller. Importantly, it remains fully compatible with standard Kubernetes service configurations.
For those considering a service mesh, Cilium presents an efficient solution. It eliminates the need for sidecars in implementing mTLS between microservices. The Cilium Service Mesh provides this functionality in a sidecar-less manner, along with HTTP routing and exceptional visibility and observability features.
At copebit, we have developed extensive expertise in integrating these two key Cilium functionalities.
Enhanced Container Services
Application and Benefits of Isovalent Tetragon for Enhanced Client Security in copebit’s Kubernetes Services
Isovalent Tetragon, a cutting-edge eBPF-based security tool, offers a strategic edge for copebit’s clients in safeguarding their Kubernetes clusters. Operating at the kernel level, Tetragon provides unparalleled real-time monitoring and control over application-kernel interactions. Its heuristic analysis capability efficiently identifies patterns that indicate security risks, enabling copebit to offer its clients a proactive defense mechanism. This approach significantly elevates container security, surpassing traditional methods like admission controllers and scanning tools, to ensure immediate and comprehensive protection against emerging threats for copebit’s clients.
Key Benefits for copebit’s Clients:
1. Real-Time Security Insights: With Tetragon’s kernel-level monitoring, clients gain instant visibility into their Kubernetes environments, enhancing their ability to swiftly detect and respond to threats.
2. Advanced Threat Prevention: Tetragon’s heuristic analysis enables copebit to detect potential threats early, offering clients proactive measures to protect their business operations.
3. Simplified Security Management: The implementation of Tetragon integrates and streamlines security processes, reducing the complexity of managing multiple security solutions for clients.
4. Customized Security Strategies: Tetragon’s adaptability allows copebit to develop tailored security policies for each client, aligning with their unique business requirements and security objectives.
5. Comprehensive Security Coverage: By combining Tetragon with existing security tools, copebit provides clients a layered and effective security strategy, ensuring robust protection in a dynamic threat landscape.
This integration of Isovalent Tetragon into copebit’s service offerings enhances the firm’s capability to deliver custom, comprehensive, and proactive security solutions, ensuring that clients’ applications and infrastructures remain secure and resilient against evolving cyber threats.
Kubernetes and Isovalent
copebit provides a range of solutions leveraging AWS EKS and Kubernetes. These solutions now include preinstalled Cilium, Hubble, and Tetragon. As an official partner of Isovalent, copebit is also equipped to offer Isovalent’s enterprise solutions.
Call to Action
See our packaged offering for AWS EKS, also with a Cilium option from just 9’500 CHF. Find the offer here.
